The ILOVEYOU Virus: A Devastating Cyberattack Of The Early 2000s
What is the "iloveyou" bug?
A computer virus, formally known as the "Love Bug" or "LoveLetter," is a type of malware that proliferated through email in 2000, causing significant damage to computer systems globally.
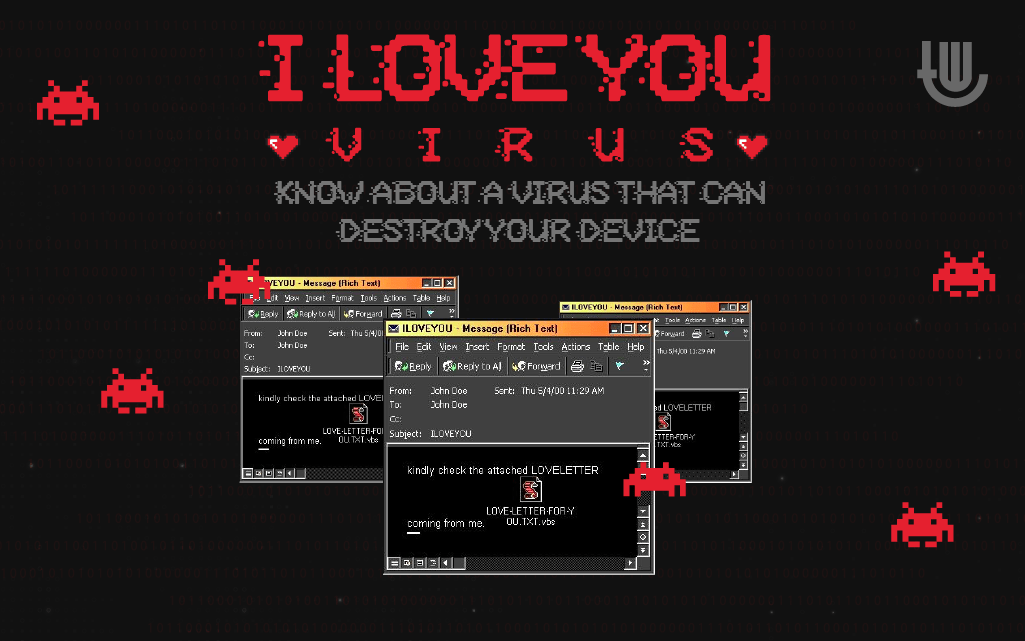
Upon opening an email attachment labeled "LOVE-LETTER-FOR-YOU.TXT.vbs," the virus would trigger, exploiting a vulnerability in Microsoft Outlook to propagate itself to every contact in the victim's address book. The virus not only disrupted email systems but also infected attached files, rendering them inaccessible.
The "iloveyou" bug was particularly devastating due to its rapid spread and the scale of damage it inflicted. It infected an estimated 10% of internet-connected computers, causing an estimated $10 billion in damages. The virus served as a wake-up call, highlighting the need for robust cybersecurity measures and raising awareness about the potential consequences of malicious software.
To prevent and mitigate the impact of viruses like the "iloveyou" bug, individuals should practice caution when opening email attachments, particularly those from unknown senders. Additionally, it is crucial to maintain updated antivirus software and operating systems, as they often include patches to address security vulnerabilities.
iloveyou bug
The "iloveyou" bug, a malicious computer virus that wreaked havoc in 2000, serves as a stark reminder of the devastating impact cyber threats can have. Its widespread infection and the damage it inflicted underscore the need for robust cybersecurity measures and vigilance against online threats.
- Origin: Email attachment disguised as a love letter
- Exploit: Vulnerability in Microsoft Outlook
- Impact: Infected 10% of internet-connected computers
- Damage: Estimated $10 billion in losses
- Propagation: Spread through email address books
- Aftermath: Heightened awareness of cybersecurity
- Prevention: Antivirus software, security updates
The "iloveyou" bug exploited human curiosity and the widespread use of email, demonstrating the potential for malicious actors to leverage social engineering tactics for their attacks. It also highlighted the importance of regularly updating software and maintaining robust cybersecurity practices to mitigate the risks posed by evolving cyber threats.
Origin
The "iloveyou" bug's origin as an email attachment disguised as a love letter played a crucial role in its widespread success and devastating impact.
- Curiosity and Trust: The use of a love letter as a lure exploited human curiosity and trust, enticing victims to open the attachment without hesitation.
- Social Engineering: The virus capitalized on social engineering techniques, leveraging the desire for romance and personal connection to trick users into executing the malicious payload.
- Lack of Awareness: In 2000, email attachments were a relatively new concept for many users, and there was less awareness about the potential risks associated with opening them.
The combination of these factors created a perfect storm, allowing the "iloveyou" bug to spread rapidly and infect millions of computers worldwide. This incident underscored the importance of cybersecurity education and the need for users to be cautious when interacting with email attachments, especially those from unknown senders.
Exploit
The "iloveyou" bug exploited a vulnerability in Microsoft Outlook, specifically its ability to execute Visual Basic scripts (VBS) from email attachments. This vulnerability allowed the virus to bypass traditional security measures and infect computers when users opened the malicious attachment.
- VBS Script Execution: Microsoft Outlook's default settings allowed VBS scripts in email attachments to run automatically, giving the "iloveyou" bug a direct path to infect systems.
- Social Engineering: The virus leveraged social engineering tactics to trick users into opening the attachment, often disguised as a love letter or other innocuous content.
- Lack of Security Updates: Many users at the time had not applied the latest security updates for Microsoft Outlook, leaving their systems vulnerable to the exploit.
- Rapid Spread: The combination of the vulnerability and social engineering techniques allowed the "iloveyou" bug to spread rapidly, infecting millions of computers worldwide in a matter of days.
The "iloveyou" bug's exploitation of a vulnerability in Microsoft Outlook highlights the importance of software updates, security patches, and user education in preventing cyberattacks. It also underscores the need for organizations to implement layered security measures to mitigate the risks posed by vulnerabilities and social engineering tactics.
Impact
The "iloveyou" bug's massive impact, infecting 10% of internet-connected computers, underscores its destructive capabilities and the far-reaching consequences of cyberattacks.
- Widespread Infection: The "iloveyou" bug's rapid spread demonstrated the ease with which malware can exploit vulnerabilities and infect a vast number of systems, regardless of their location or industry.
- Severe Disruption: The virus disrupted email systems, corrupted files, and caused widespread network outages, resulting in significant downtime and productivity losses for businesses and organizations.
- Economic Losses: The "iloveyou" bug caused an estimated $10 billion in damages, highlighting the financial impact of cyberattacks and the need for robust cybersecurity measures.
- Heightened Awareness: The widespread impact of the "iloveyou" bug raised public awareness about the threats posed by malware and the importance of cybersecurity.
The "iloveyou" bug's impact serves as a cautionary tale, underscoring the need for organizations and individuals to prioritize cybersecurity, implement robust security measures, and remain vigilant against evolving cyber threats.
Damage
The "iloveyou" bug's devastating impact extended beyond widespread infections and network disruptions, resulting in an estimated $10 billion in financial losses. This staggering figure underscores the severe economic consequences that cyberattacks can inflict upon businesses, organizations, and individuals.
The virus's destructive capabilities caused significant downtime, disrupted operations, and compromised sensitive data, leading to lost productivity, revenue, and reputational damage. The financial losses incurred by businesses included the cost of repairing infected systems, recovering lost data, and implementing enhanced security measures to prevent future attacks.
The "iloveyou" bug's economic impact serves as a stark reminder of the importance of cybersecurity and the need for organizations to prioritize their digital defenses. By investing in robust security measures, businesses can mitigate the risks of cyberattacks and protect their financial interests.
Propagation
The "iloveyou" bug's propagation method, leveraging email address books, played a critical role in its rapid and devastating spread across the globe.
When a victim opened the malicious email attachment, the virus exploited a vulnerability in Microsoft Outlook to access the victim's email address book. It then automatically sent copies of itself to every contact in the address book, continuing the cycle of infection.
This propagation method proved highly effective, as it allowed the virus to spread exponentially, reaching a vast number of computers in a short period of time. The ease with which the virus could self-propagate, combined with its ability to infect multiple file types, contributed to its widespread impact and the significant damage it caused.
Understanding the propagation mechanism of the "iloveyou" bug is crucial for developing effective strategies to prevent and mitigate future cyberattacks. By implementing robust email security measures, such as email filtering and anti-malware software, organizations can reduce the risk of infection and protect their systems from similar threats.
Aftermath
The "iloveyou" bug's devastating impact and widespread media coverage sparked a global wake-up call regarding cybersecurity threats and the importance of robust digital defenses.
Prior to this incident, cybersecurity was often overlooked or considered a secondary concern for many organizations and individuals. However, the "iloveyou" bug's destructive capabilities demonstrated the potential for cyberattacks to cause significant financial losses, disrupt operations, and damage reputations.
In the aftermath of the attack, governments, businesses, and individuals alike recognized the urgent need to prioritize cybersecurity and implement comprehensive security measures. This heightened awareness led to increased investment in cybersecurity technologies, the development of new security protocols, and a greater emphasis on cybersecurity education and training.
Moreover, the "iloveyou" bug exposed the interconnected nature of the digital world and the ease with which cyberattacks could spread across borders. This realizationinternational collaboration on cybersecurity initiatives, such as the formation of the Budapest Convention on Cybercrime, to combat cyber threats and promote global cooperation.
Today, cybersecurity remains a critical concern for organizations and governments worldwide. The lessons learned from the "iloveyou" bug continue to shape cybersecurity practices and inform strategies to prevent and mitigate future cyberattacks.
Prevention
The devastating impact of the "iloveyou" bug underscored the critical importance of antivirus software and regular security updates as essential components of a comprehensive cybersecurity strategy.
Antivirus software is designed to detect and neutralize malicious software, including viruses, worms, and Trojans, before they can infect a computer system. By regularly updating antivirus software, users can ensure that they have the latest protection against emerging threats. Similarly, security updates for operating systems and software applications patch vulnerabilities that could be exploited by attackers to gain unauthorized access or execute malicious code.
In the case of the "iloveyou" bug, the rapid spread of the virus was partly attributed to the fact that many users had not applied the latest security updates for Microsoft Outlook, which left their systems vulnerable to the exploit used by the virus. Had these updates been installed, the impact of the virus could have been significantly reduced.
Today, antivirus software and security updates remain essential elements of cybersecurity hygiene. By implementing these measures, individuals and organizations can proactively protect their systems from a wide range of cyber threats, including those similar to the "iloveyou" bug.
Frequently Asked Questions about the "iloveyou" Bug
The "iloveyou" bug, a devastating computer virus that emerged in 2000, raised significant concerns and prompted numerous inquiries. Here are answers to some of the most frequently asked questions surrounding this infamous cyberattack:
Question 1: What was the impact of the "iloveyou" bug?
The "iloveyou" bug had a profound impact, infecting an estimated 10% of internet-connected computers worldwide. It caused widespread disruptions to email systems, corrupted files, and led to significant financial losses, estimated at around $10 billion.
Question 2: How did the "iloveyou" bug spread?
The virus primarily spread through email, disguised as a love letter with an attachment labeled "LOVE-LETTER-FOR-YOU.TXT.vbs." When users opened the attachment, it exploited a vulnerability in Microsoft Outlook to replicate itself and spread to all contacts in the victim's address book.
Question 3: What were the vulnerabilities exploited by the "iloveyou" bug?
The virus exploited a vulnerability in Microsoft Outlook that allowed it to execute Visual Basic scripts (VBS) from email attachments. Many users at the time had not applied the latest security updates for Microsoft Outlook, which left their systems vulnerable to the exploit.
Question 4: What measures can be taken to prevent similar attacks in the future?
To prevent similar attacks, it is crucial to maintain updated antivirus software, apply security updates for operating systems and software applications, and exercise caution when opening email attachments, especially from unknown senders.
Question 5: What lessons were learned from the "iloveyou" bug attack?
The "iloveyou" bug attack highlighted the importance of robust cybersecurity measures, the need for regular software updates, and increased awareness about social engineering tactics used by attackers.
Question 6: What is the significance of the "iloveyou" bug in cybersecurity history?
The "iloveyou" bug is considered a significant event in cybersecurity history. It demonstrated the devastating impact of cyberattacks, raised public awareness about cybersecurity threats, and led to verstrkte emphasis on cybersecurity practices and international collaboration.
The "iloveyou" bug serves as a reminder of the evolving nature of cyber threats and the importance of staying vigilant and proactive in defending against them.
Moving forward: Cybersecurity Best Practices
Conclusion
The "iloveyou" bug, a devastating computer virus that emerged in 2000, serves as a stark reminder of the evolving nature of cyber threats and the critical importance of robust cybersecurity measures. Its widespread impact, infecting millions of computers and causing billions of dollars in damages, underscores the need for organizations and individuals alike to prioritize digital defenses.
The "iloveyou" bug exploited vulnerabilities in software and human behavior, highlighting the importance of regular security updates, antivirus software, and caution when interacting with email attachments. The attack also raised awareness about social engineering tactics used by attackers to trick users into executing malicious code.
Moving forward, it is essential to remain vigilant and proactive in defending against cyber threats. By implementing comprehensive security measures, educating users about cybersecurity best practices, and fostering international collaboration, we can mitigate the risks posed by malicious actors and protect our digital infrastructure.


Detail Author:
- Name : Kavon Mante
- Username : schumm.kathryne
- Email : unienow@roob.net
- Birthdate : 2000-08-13
- Address : 22251 Jay Brooks Edwardomouth, TN 71838-9620
- Phone : +1-262-487-6793
- Company : Predovic-Schinner
- Job : Architect
- Bio : Iste iure quos sunt at mollitia. Laboriosam sapiente alias autem quae voluptates velit odio. Eos sit quam nostrum quasi maiores. Velit ad minima et nihil veniam sint exercitationem.
Socials
tiktok:
- url : https://tiktok.com/@raynork
- username : raynork
- bio : Aut velit enim temporibus reiciendis fugiat. Et ex quis sunt magni tempore id.
- followers : 5388
- following : 65
instagram:
- url : https://instagram.com/khalid_raynor
- username : khalid_raynor
- bio : Voluptatibus eum sequi fugiat mollitia. Praesentium quia minus dolor est.
- followers : 438
- following : 2012